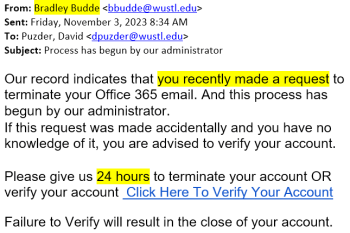
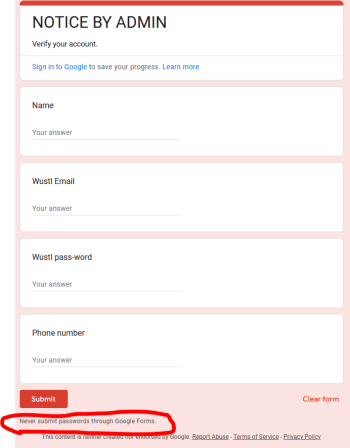
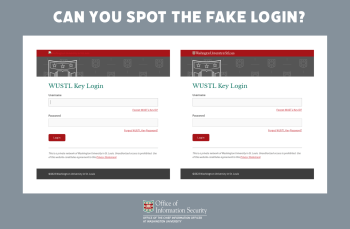
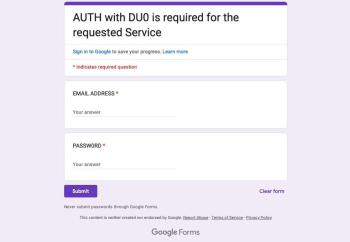
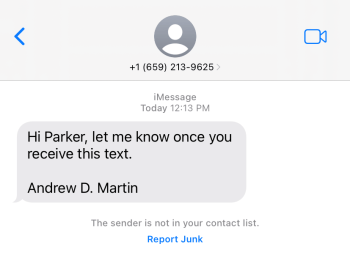
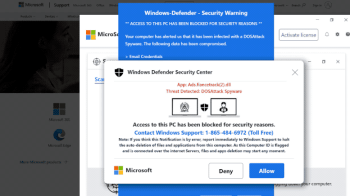
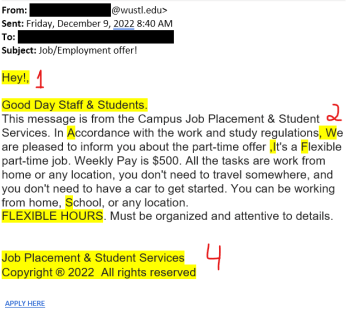
The Office of Information Security has identified a trend in which criminals send members of our community account termination emails containing a malicious link. They hope a victim will give their WashU credentials in a Google Form. In this scam, hackers use a legitimate WashU email address to send phishing emails. Victims who click the […]
Scam of the Month: Process has begun by our administrator