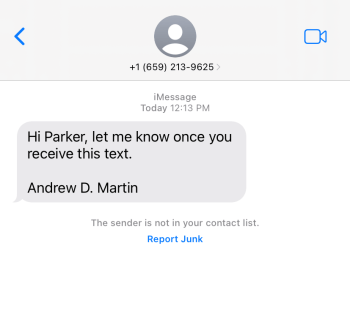
The Office of Information Security has observed a trend in which criminals impersonate Chancellor Andrew Martin over text message. Impersonation is one of the most effective social engineering tactics used by scammers, and it can be particularly powerful when the person being impersonated is in a position of authority.
If you see a message like the one below, please do not interact with the sender and do not follow any special instructions. When in doubt, you can always reach out to the person being impersonated using known contact methods. Please be aware of the following tips for recognizing these types of tech support scams.
- Gift card requests are almost always a scam.
- Requests to change where wire transfers are sent are almost always a scam.
- Another common scam involves asking the recipient to wire money because the impersonated party is in a foreign location and lost their wallet.
- Any time that money or resource transfer is part of a request, you should exercise extreme caution. There are many ways to transfer money and resources these days, so be on the lookout for scammers to attempt them all.
- If you receive anything resembling what has been described above, it is best to reach out to the person, office, institution, etc., using a known contact method. Please never reach out by replying directly to the message, following any links in it, or using any contact info it contains.
Here are some helpful tips for avoiding a scam like this one:
If you receive a suspicious text message, the best action to take depends on the situation. Since texts aren’t transmitted using managed WashU IT systems, you will often need to reach out to your specific provider.
- If it’s clearly fake, report it.
- If you aren’t sure if it’s a fake, use a known contact method to verify the text.
- If you get a very vague and tentative message like “How are you?” or even just your name (or someone else’s) with a question mark, we recommend ignoring it or reporting it.
- It is risky to respond with a question like “Who is this?” because the bad guys now know you’re there and will try to engage you, first from the same number but then in other ways from other numbers.
- If someone you know is trying to connect to you from a new number, it’s their obligation to properly identify themselves, explain themselves, and not ask you for gift cards.
Additional Resources
Phishing | Office of Information Security | Washington University in St. Louis
Phishing 101 | Office of Information Security | Washington University in St. Louis
Vishing | Office of Information Security | Washington University in St. Louis (wustl.edu)