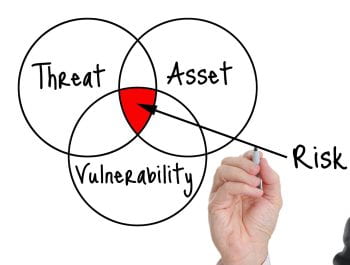
A campus-wide initiative is underway to improve computer security by installing the Splunk Forwarder and CrowdStrike on all servers by the end of June, as InfoSec Policy requires. The Splunk Forwarder gathers real-time log data from servers into a searchable repository. This log data can help detect and troubleshoot security incidents quickly and efficiently. CrowdStrike, […]
Splunk and CrowdStrike Server Installation Initiative