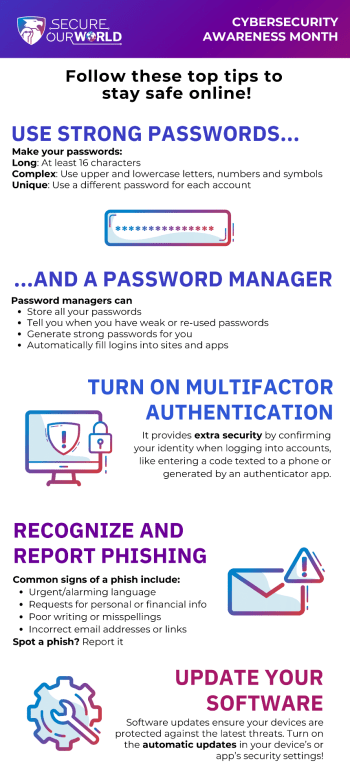
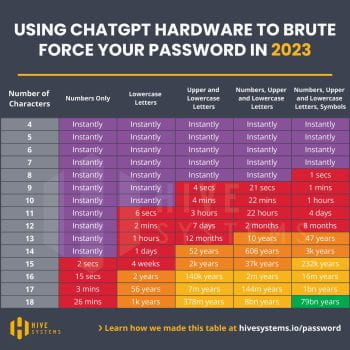
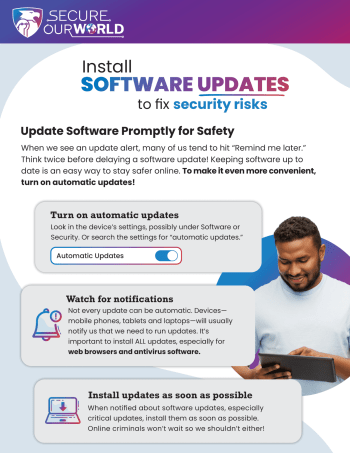
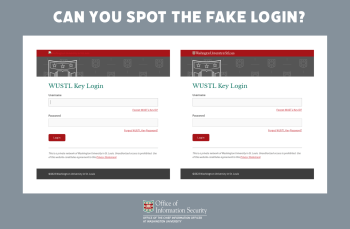
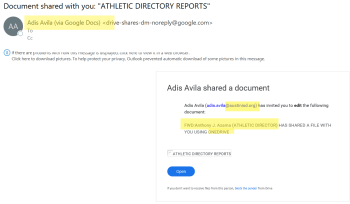
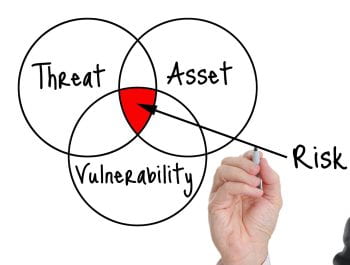
As attackers figure out new ways to get around traditional multi-factor authentication, we must evolve to prevent fraudulent access to our accounts. The next wave of multi-factor authentication will fortify user accounts against phishing attacks. Unlike traditional multi-factor authentication, new approaches incorporate advanced techniques such as biometric authentication, hardware tokens, and push notifications to trusted […]
Phishing Resistant Multi-Factor Authentication