Letter from the CISO, Vol 2 Issue 10 Washington University Community: I often encourage everyone to “be vigilant, skeptical, and a little paranoid,” and I usually provide a few pointers on things to watch out for and what to do when (if) you see them. Which Half Are You In? A recent report concluded that […]
Tag: Letter
Keeping Information Security Simple – Top Lies: Spy Balloons, Earthquakes, and Romance Scams
Letter from the CISO, Vol 2 Issue 9 Washington University Community: Rule #1: Be Vigilant, Skeptical, and a Little Paranoid Cybercriminals and scammers are constantly changing and adapting, trying new ways to take advantage of us. Therefore, I return to the one thing I challenge you to do – be vigilant, skeptical, and even a […]
Keeping Information Security Simple – Artificial Intelligence Has Arrived, and You Should Pay Attention
Letter from the CISO, Vol 2 Issue 8 Washington University Community: There has been a lot of news lately about the exciting and alarmingly adept Artificial Intelligence (AI) known as ChatGPT, which may be able to pass Alan Turing’s famous test of being indistinguishable from real (human) intelligence. Some say this is the beginning of […]
Keeping Information Security Simple – Am I Smarter than a Sixth Grader? – Protecting our Families Online
Letter from the CISO, Vol 2 Issue 7 Washington University Community: Am I Smarter than a Sixth Grader? I like to think so, but the evidence suggests otherwise. At least when it comes to figuring out how to limit the trouble my young nieces can get into on their mobile devices. Yes, their mother, father, […]
Keeping Information Security Simple – Your Internet Bodyguard
Letter from the CISO, Vol 2 Issue 6 Washington University Community: High School Bodyguard? When a friend’s daughter was in high school, she had written to a German exchange student who was coming to the US, writing about her kickboxing class and her job as a lifeguard at the neighborhood summer swim club. Unfortunately, when […]
Keeping Information Security Simple – You’re smart and getting smarter, but…
Letter from the CISO, Vol 2 Issue 5 Washington University Community: Everyone loves to hear how smart they are! Right? I don’t know anyone who doesn’t like hearing how they are “smart,” “bright,” “clever,” “hard-working,” “correct,” and best of all, “you’re right; I was wrong.” Today I have good news, better news, bad news, and […]
Keeping Information Security Simple – It’s All About “The Hook”
Letter from the CISO, Vol 2 Issue 4 Washington University Community: What’s the best defense against the phishing attacks responsible for over 90% of cyber intrusions and breaches? The simple answer is all of us working together. And “The Hook.” Given time, attention, basic suspicion, and a little paranoia, we can all individually spot most […]
Keeping Information Security Simple – Help Yourself by Helping Others
Letter from the CISO, Vol 2 Issue 3 Washington University Community: Want to know how to be “enough” of an information security expert? In “Outliers,” Malcolm Gladwell popularized the idea of needing 10,000 hours of practice to become an expert. I studied karate for many years, and one of my sensei’s (instructor’s) expectations was that […]
Keeping Information Security Simple – Why Do Cars Have Brakes?
Letter from the CISO, Vol 2 Issue 2 Washington University Community: Why Do Cars Have Brakes? Why do cars have brakes? The obvious answer is that it helps them slow down and stop. The “real” counter-intuitive reason is that brakes let cars go fast. Imagine the panic and fear of being in a car that […]
Keeping Information Security Simple – Who’s Responsible for Information Security?
Letter from the CISO, Vol 2 Issue 1 Washington University Community: Who’s responsible for Information Security at WashU? It seems like an odd question for me to ask since I’m the Chief Information Security Officer, but I ask it anyway. I know information security is my responsibility. Or, at least, it’s usually the person in […]
Keeping Information Security Simple – Phishing, Spear Phishing & Whaling
Letter from the CISO, Vol 1 Issue 12 Washington University Community: Do you know the differences between phishing, spear-phishing, and whaling? Let’s start with the difference between phishing and spear phishing. In short, phishing messages are those all-too-familiar messages that try to get you to give away information or install malware. They arrive via email, […]
Keeping Information Security Simple – The Only Constant in Life is Change
Letter from the CISO, Vol 1 Issue 11 Washington University Community: There are only two things to worry about—that things will never get back to normal, or . . . that they already have. In other words, the only constant in life is change, and Information Security is no exception. I sometimes worry that I […]
Keeping Information Security Simple – Device Management – March 2022
Letter from the CISO, Vol 1 Issue 10 Washington University Community: This month I’m going to bore you with another really basic idea: that everyone needs to manage their devices. I can almost hear you yawning when I write those words, but it’s essential and not quite as easy as you might think. Step 1: […]
Security Spring Cleaning Top Five

Spring has arrived, and with it, the age-old tradition of spring cleaning. Getting organized, cleaning up your computer, and checking on your security hygiene will make your life easier as you approach the end-of-semester push toward summer adventures! As you clear away the cobwebs and shake off the dust of winter, also remember to clean […]
Another Chance to Win and New Defender Features Coming to Office 365

The OIS is always looking for ways to improve your security and reward your participation in our efforts. This month, we’re introducing new security features in Office 365 and running another prize competition! March Prize Giveaway We had a great turnout for our February Information Security prize giveaway, so we’re doing it again this month! […]
Scam of the Month: Ukraine Donation Scam
This month, we’re focusing on another scam that preys on your emotions and altruistic intentions. This time, it involves cybercriminals taking advantage of fundraising for Ukraine. In just one week, legitimate fundraising for Ukraine mobilized more than $50 million in cryptocurrency. That kind of success always attracts opportunists who want their cut. This time, they’re […]
Meet Your InfoSec Team: Quint Smith, Information Security Training and Communications Manager

For the past three years, Quint Smith, Information Security Training and Communications Manager, has been building and managing the InfoSec marketing, communications, and culture program. He aims to encourage an informed, aware, and empowered user community, resilient to the continually evolving cyber threat landscape. He says, “information security is an arms race, and technical defenses […]
Electronic Waste & Paper Shredding Drives this March

On Tuesday, March 22 and Tuesday, March 29, the Operations & Facilities Management Department, the Office of Sustainability, and WashU’s Office of Information Security are teaming up to bring the WashU community e-waste recycling and confidential paper shredding services. All are welcome to bring accepted items to the collection drive. All confidential papers and hard […]
Increased Risk of State-Sponsored Cyberattacks as Russia Invades Ukraine

The threat of state-sponsored cyberattacks increasingly accompanies international relations. Russia has developed and demonstrated its capacity to attack and inflict damage using cyber-warfare tactics. With news of Russia’s invasion of Ukraine, many cybersecurity professionals are recommending increased vigilance during this period of unrest. While much of the responsibility for anticipating and preventing cyberattacks of this […]
Keeping Information Security Simple – Isn’t there an App for that?
Letter from the CISO, Vol 1 Issue 9 Washington University Community: This month I’d like to warn you about dangerous applications and Internet services, and four things you can do to avoid problems. Many experts focus on iPhone/iPad/iOS and Android devices, but PC and Macs are also vulnerable to malicious applications, so I’ll speak about […]
10 Security Tips for Spring-Break Travelers

Spring Break is on the horizon, and many in the WashU community plan to travel for conferences, study away, research opportunities, and maybe even a little rest and relaxation! Smartphones and other digital devices are an integral part of our everyday lives, and they can make travel seem like a blissful dream. Helpful capabilities—your digital […]
Security Tips for Working From Home

By now, we’re all intimately familiar with the benefits and drawbacks of working from home. You may have been working from home for most of the pandemic, are a hybrid employee, or simply take your work or devices home for breaks and weekends. Whatever your unique situation, you probably have direct experience walking the increasingly […]
Seven Lucky Winners and More Chances to Win Prizes!

The results of our 2021 Cybersecurity Awareness Month competitions are in! Our office has selected seven lucky winners. If you’re a winner, we will contact you at your WUSTL email address to request the information we need to deliver your award. If you didn’t win this time, don’t despair! Read on for information about future […]
Scam of the Month: Fake Norton or Geek Squad Call Scam

Attackers are using criminal Gmail accounts to target members of our institution with a phishing scam that involves requesting the recipient call a phone number for additional information. The attackers use dozens of Gmail accounts, using each account to target only one or a few users and modifying minor details to avoid detection. As a […]
Meet Your InfoSec Team: Bob Therina, Information Security Analyst II

Bob Therina, Information Security Analyst II, came to Information Security after training and working in Computer Technology and the IT-sphere more broadly. He humbly reports that he sees himself as a generalist rather than an expert, capable of working across the IT space, building bridges between colleagues with deep expertise in a variety of areas. […]
Keeping Information Security Simple – Privacy – Free isn’t free: If you aren’t paying for it, you and your data are the product being sold!
Letter from the CISO, Vol 1 Issue 8 Washington University Community: This is the National Cybersecurity Alliance’s Data Privacy Week (https://staysafeonline.org/data-privacy-week/), and because security is closely related to privacy, I thought I’d say a few things about it. The “right to privacy” was defined by Justice Louis Brandeis in an 1890 article as the right […]
Threats to Your Research Data and Intellectual Property

Your research data and intellectual property are valuable, not only in the pursuit of knowledge for the betterment of society but also to cybercriminals who seek to steal it or hold it for ransom. According to the Federal Bureau of Investigation , intellectual property theft is a growing threat in the digital era, and much […]
Phishing Awareness Phase II: Competition Winners to be Notified
The Office of Information Security recently added several layers of phishing protection for our institution. We hope you have located, and perhaps even used, the new Phish Alert Button (PAB). Last week, our office distributed our first university-wide message from the KnowBe4 platform, asking users to report it as a phish using the PAB to […]
Security Advice from a Busy Student

By Jack Ballenger (Class of 2024) During these two weeks of virtual classes, students will need to use Duo Mobile, an app for two-factor authentication (2FA), to access Canvas, Outlook, WebStac, and other WashU resources since they are not connected to campus WiFi. Two-factor authentication, also called multi-factor authentication (MFA) or two-step authentication, supplements your […]
How to Take Back Control of Your Data This Data Privacy Week

Adapted from The National Cybersecurity Alliance, January 2022 From social media to online shopping, our lives and the digital world become more intertwined every day. The digital world affords us a new level of convenience and access to information, but there may be a hidden cost to your privacy associated with these conveniences. Consumers must […]
Data Privacy Fast Facts

Adapted from National Cybersecurity Alliance In Case You Missed It Protecting the World’s Most Valuable ResourceWashington University Office of Information Security, December 2021
Scam of the Month: SMiShing and 3 Viruses Detected Scam
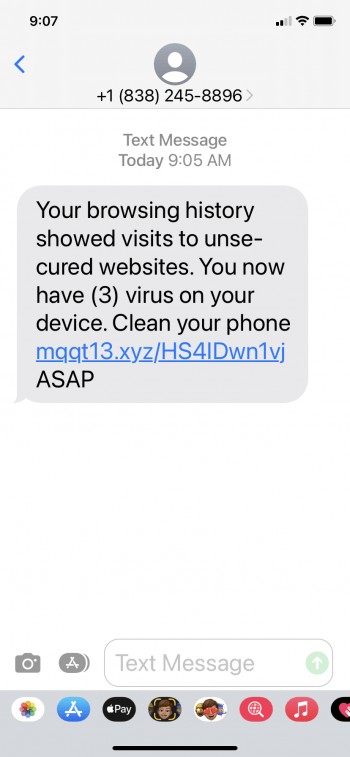
The Office of Information Security has received reports of a SMiShing campaign targeting people at our institution. SMiShing occurs when cybercriminals use tactics common to phishing campaigns in text messages, attempting to communicate legitimacy to their unsuspecting victim. The reported scam (pictured below) is a text-based version of a common and long-running scam that is […]
Meet Your InfoSec Team: Christina Pomianek-Smith, Policy and Risk Analyst

Information security involves solving complex problems, incorporating diverse perspectives to address the technical, legal, social, and behavioral dimensions of the digital era. Christina Pomianek-Smith’s recent move into information security demonstrates the multidisciplinary demands of the field. She is a cultural anthropologist by training (PhD, University of Missouri—Columbia, 2012), with research interests in trust, cooperation, and […]
Keeping Information Security Simple – Automagically update everything!
Washington University Community: Modern computers and mobile devices are so complex that they invariably have unintended flaws. Some of these flaws create vulnerabilities by which cybercriminals can attack your computer, tablet, or phone. In fact, these vulnerabilities are one of the most common ways devices are hacked. The good news is that it is surprisingly […]
Keeping Information Security Simple – There’s no better feeling than recovering your lost device!
Washington University Community: Have you ever lost your phone, tablet, or computer? Or maybe just not been able to find it? Of course, you have (probably)! It happens all the time. Just last week, I had my dogs at a dog park, and as I was preparing to leave, about 250 pounds of playing dogs […]
Keeping Information Security Simple – Backup, Backup, Backup
Letter from the CISO, Vol 1 Issue 5 Washington University Community: Many years ago, a respected colleague told me that for her, the ultimate security was knowing that she could get her data back if something bad happened. This was a bit of a shock to me, as I was young and inexperienced enough to […]
Keeping Information Security Simple – Physical Security Comes First
Letter from the CISO, Vol 1 Issue 4 Washington University Community: Physical safety is a fundamental need of all animals, humans, computer systems, and devices. Last month I encouraged everyone to adopt a healthy dose of skepticism and paranoia regarding email, text, and social media messages to avoid becoming victims of social engineering attacks. This […]
Keeping Information Security Simple – Be Skeptical and a Little Paranoid
Letter from the CISO, Vol 1 Issue 3 Washington University Community: “Keep Information Security Simple” has been my motto for nearly a decade. This month, I’d like to share an important thing that everyone can do to improve our security—slow down, just a little bit because haste makes good people fall for bad tricks. In the first […]
Keeping Information Security Simple – Multi-Factor Authentication
Washington University Community: Thank you for the positive feedback on June’s first issue of our new Information Security Bulletin, “Secured!” If you missed it, you can read it and other articles of interest at https://informationsecurity.wustl.edu/blog/. For almost a decade, I’ve been trying to “Keep Information Security Simple” (KISS) for my clients, employers, and friends. KISS is […]
Letter from the CISO – Everyone is in InfoSec
Washington University Community: I welcome you to this inaugural edition of our new Information Security Bulletin. My primary goal for the bulletin is to empower every member of our community to do their part in protecting us from cybersecurity attacks. A few years ago, the CISO for a health system was asked how many people […]