Keeping Information Security Simple – “It’s Much Too Easy to Be Stupid”
Letter from the CISO, Vol 3 Issue 11 Washington University Community: Failing to be smart is easy… Writing to the Washington University in St. Louis community, I don’t expect disagreement that it is better to be smart than the opposite. However, even the smartest people can have moments of stupidity. In a recent interview with […]
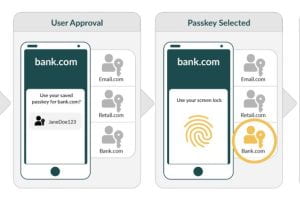
Passkeys Over Passwords
Are you tired of trying to create and remember every password? Are you worried that you might lose your password? Do you feel overwhelmed by the number of password managers to choose from? If so, there is good news on the horizon. The FIDO Alliance created a passwordless sign-in system that addresses these problems, and […]
Chance to Win $100 in Our Monthly Challenge
The Office of Information Security (OIS) is always looking for ways to improve your security and reward your participation in helping to secure WashU. Back by popular request, the InfoSec team is assigning the Inside Man as our training competition this April. The Inside Man is a soap opera-style training that covers critical cyber security […]
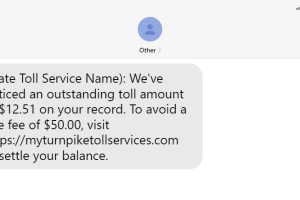
Scam of the Month: Outstanding Toll Amount
Road trip season is approaching, and the FBI has observed criminals impersonating road toll collection services via text message. While there is only one toll bridge in Missouri – the Lake of the Ozarks Community Bridge (for now) – many neighboring states operate toll roads. If you see a message like the one below, please […]
Summer Break Travel and Job-Hunting Tips
Summer break is right around the corner, and many in the WashU community will be traveling or looking for a summer job. Unfortunately, the devices we rely on for managing travel have also become targets for theft and cybercrime. Whether you are searching for a job or taking a trip, please protect yourself and the […]
Meet Your InfoSec Team: Joey Smith, Information Security Analyst III
Joey Smith, Information Security Analyst III, works in the OIS Clinical Operations team, focusing on the School of Medicine and the Medical Campus. Joey uses tools to identify and monitor unmanaged devices on the WashU network. This effort assists in ongoing projects like asset management and network asset control (NAC). Joey enjoys IT and security […]
Keeping Information Security Simple – “Denial is not a river in Egypt!”
Letter from the CISO, Vol 3 Issue 10 Washington University Community: Criminals keep inventing new con attacks I recently saw a news report about a Mexican drug cartel that has gotten into the business of helping elderly Americans get out of the timeshare vacation contracts. This sounds like a good thing. Unfortunately, it is just […]
Chance to Win $100 in Our Monthly Challenge
The OIS is always looking for ways to improve your security and reward your participation in our efforts. Back by popular request, the InfoSec team is assigning the Inside Man as our training competition this March. The Inside Man is a soap opera-style training that covers critical cyber security themes in all its episodes. Watch […]
Reporting Phishing in the ‘New’ Outlook
The Phish Alert Button (PAB) is one of our team’s most valuable tools for keeping the WashU community safe. When you report a phishing email using the PAB, our office will investigate the threat and take any necessary action, such as removing all similar messages from systems and notifying our community of the danger. If […]
Scam of the Month: DEA Impersonation Phone Call
According to Washington University School of Medicine Protective Services, the WUSM Physical Therapy department received a call from someone impersonating the DEA to steal personally identifiable information. In the call, they claimed to be an investigator from the DEA headquarters, saying that a nurse practitioner had reported fraud under their name, medical license number, and […]
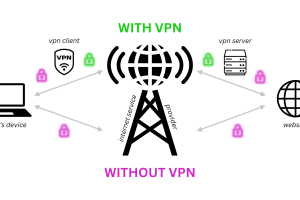
The Power of Virtual Private Networks (VPN) in Privacy Protection
In the digital age where a lot of our private information is on the internet – in public and supposedly in private storage – ensuring online privacy has become even more integral to protecting your online activity and identity. According to Cobalt’s Top Cybersecurity Statistics for 2024, there are over 2,200 cyberattacks a day (a […]
The Deaf Lottery Scam
Back in his federal law enforcement days, WUSM’s Assistant Director of Investigations and Crime Prevention, Steve Manley, came upon an advance fee scam. An informant who operated a corner store in East St. Louis called him one afternoon. He told Manley a customer was sending large sums of money to Nigeria via Western Union. The caller […]
Thanks for Making the E-Waste Recycling Event a Success
On Tuesday, March 26th, the Office of Sustainability and Office of Information Security hosted their biannual electronic waste recycling and secure paper shredding event on the Danforth campus. Thank you to all who supported sustainability by securely recycling their electronic waste and confidential documents. The event was a huge success. In just two and a […]
Keeping Information Security Simple – “Using Code Words to Defeat the AI Menace”
Letter from the CISO, Vol 3 Issue 9 Washington University Community: Artificial Intelligence is a tool Artificial Intelligence, or AI, has received a lot of attention and interest over the past year, primarily due to the great advances in productivity and quality it seems to promise. WashU IT is excited to be helping the university […]
New Device Registration Process for the Wired Network on the WUSM Campus
WashU IT, Information Security, and WUSM ITSS are introducing a new registration process for devices connecting to the wired network. This change will further protect patient, student, research, and academic data from bad actors. We will begin implementing this change in early 2024. It will be rolled out in a measured pace to minimize impact […]