Letter from the CISO, Vol 2 Issue 7 Washington University Community: Am I Smarter than a Sixth Grader? I like to think so, but the evidence suggests otherwise. At least when it comes to figuring out how to limit the trouble my young nieces can get into on their mobile devices. Yes, their mother, father, […]
Tag: newsletter volume 2 issue 7
Chance to Win $100 in Our Monthly Challenge

The OIS is always looking for ways to improve your security and reward your participation in our efforts. This month, we want to point you toward a couple of resources that will help you protect yourself from cybercrime and understand how our office can support you. Guidance for Reporting Phishing Have you seen the Phish […]
Biometric-based Authentication
In the last two months, we covered password-based authentication and token-based authentication. When properly implemented and used, both methods can provide secure user authentication. Still, passwords and tokens each have their shortcomings: Complex—and therefore secure—passwords are hard to remember. A token can be lost. Either can be stolen. Meanwhile, biometric authentication uses personal data that […]
Securing New Devices

A recent market forecast predicted that the average volume of electronics per person in the Consumer Electronics market will increase to 2.8 pieces in 2022 (Consumer Electronics – US: Statista market forecast). With gift-giving season approaching, you or someone you know will likely receive some tech. Follow the strategies below to keep your shiny new […]
Scam of the Month: Job/Employment Offer
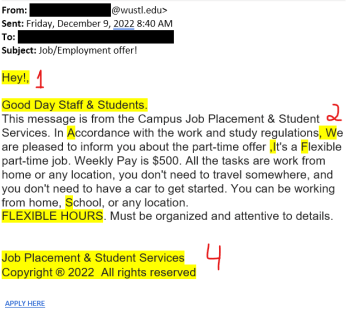
The Office of Information Security observes a trend in which criminals send fraudulent job requests, hoping that victims will click a malicious link. If you see a message like the one below, please do not interact with the sender or phone number, and don’t follow any special instructions. Simply report the email using the Phish Alert […]
Meet Your InfoSec Team: Richard Edwards IV, GRC Analyst II

Since Richard Edwards IV, Governance Risk and Compliance Security Analyst II, began working in IT, security has been his top interest. For one, he enjoys how information security challenges him to keep learning. He also noticed a trend: As technology becomes more incorporated into everyday life, so too do threats and vulnerabilities to our technology. […]