As attackers figure out new ways to get around traditional multi-factor authentication, we must evolve to prevent fraudulent access to our accounts. The next wave of multi-factor authentication will fortify user accounts against phishing attacks. Unlike traditional multi-factor authentication, new approaches incorporate advanced techniques such as biometric authentication, hardware tokens, and push notifications to trusted devices, making it significantly more challenging for attackers to impersonate users.
Phishing for One-time passcodes
Receiving a passcode by text message is simple and only requires someone to have a cell phone. Unfortunately, if an attacker already has someone’s username and password, they can trick victims into sending their one-time passcodes. Alternatively, hackers can employ the SIM swap scam to get the verification codes sent to your number.

Some accounts only offer one-time passcode authentication via text or email. It is better than no two-factor authentication; however, it is clearly vulnerable to phishing attacks.
Phishing for push-based notifications
When an attacker steals someone’s WUSTL key and password, each time they attempt to log in, the owner of the WUSTL key receives a Duo request. If push-based notifications are enabled by default, they will receive a notification from the Duo app, which they can either accept, deny, or ignore entirely. It is easy to deny or ignore one push from Duo, but what if the attacker bombards their phone with login attempts?
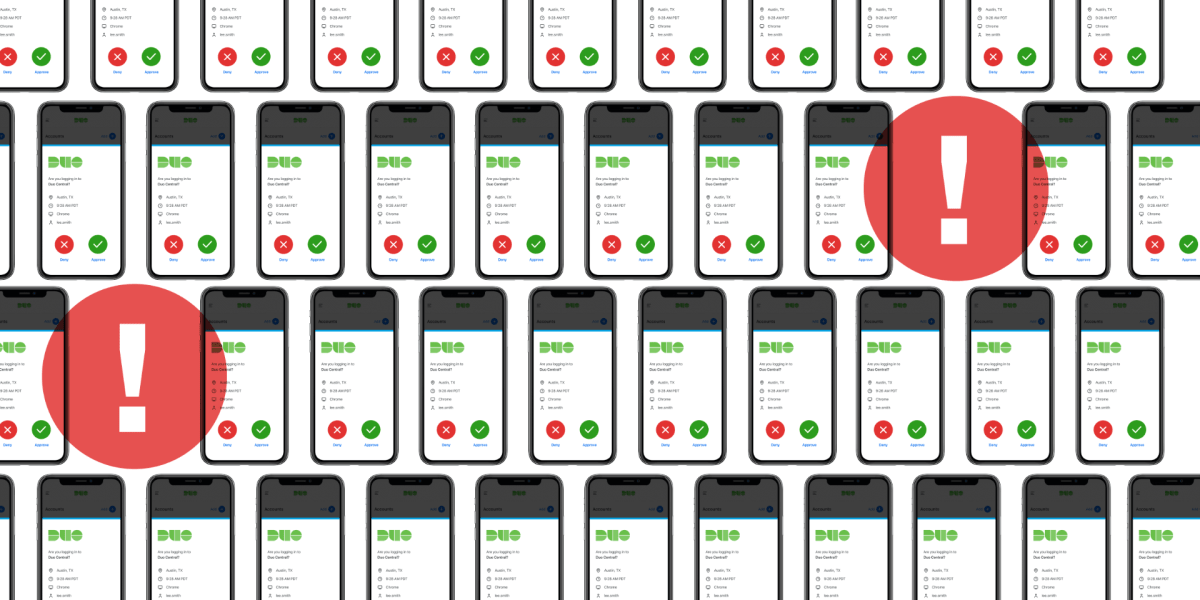
In a push phishing attack – push bombing, push harassment, or MFA fatigue attack – the attacker repeatedly sends Duo requests until the victim caves and accepts the request to stop receiving the push notifications.
Before we implemented multi-factor authentication at WashU, if an attacker had a stolen username and password, that was all they needed to gain access. Implementing Duo forced them to develop new methods to get around this defense. Cybersecurity has always been a back-and-forth between tactics and responses. Now is the time to respond.
Verified Duo Push
The next form of multi-factor authentication asks us to enter a verification code from the login screen into the Duo mobile app. Here is what that would look like:
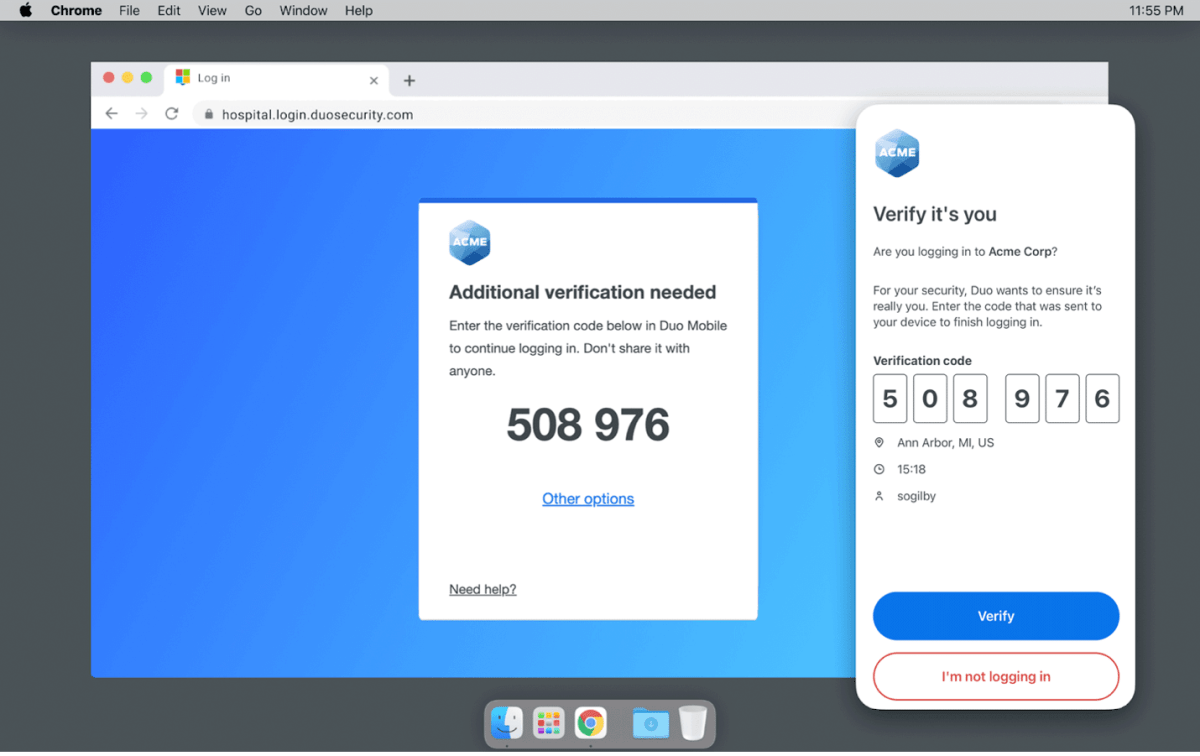
During a legitimate login, I enter my WUSTL key and password. Then, I am asked to enter a specific code in my Duo app. I enter the code, tap ‘Verify’, and get on with my work.
During an illegitimate login, an attacker enters my WUSTL key and password. Then, the login screen asks them to enter the code in my Duo app. Unless they have access to my unlocked phone, they’re not getting anywhere. If this happens, I can tap “I’m not logging in,” and Duo tells me where and when they are logging in. This implementation also ensures I can’t accidentally approve illegitimate login requests. If I don’t know the code on someone else’s screen, I can’t enter it into my app.
To learn more about verified Duo push and how it would work at WashU, please visit November 20: DUO 2FA Changes – Information Technology (wustl.edu)
Enabling Multi-factor Authentication
As time passes, more websites and applications will offer phishing-resistant multi-factor authentication. While older implementations are less secure, they are still better than single-factor authentication. Here are guides on how to enable multi-factor authentication for popular services:
- Google: Turn on 2-Step Verification – Android – Google Account Help
- Microsoft: Turning two-step verification on or off for your Microsoft account – Microsoft Support
- Apple: Two-factor authentication for Apple ID – Apple Support
- Instagram: Securing your Instagram account with two-factor authentication | Instagram Help Center
- WhatsApp: About two-step verification | WhatsApp Help Center
- Facebook: How two-factor authentication works on Facebook. | Facebook Help Center
- PayPal: How do I turn on or off 2-step verification for PayPal account login?
- Amazon: What is Two-Step Verification? – Amazon Customer Service