The Office of Information Security works diligently to protect our institution from phishing threats. Ultimately, however, our shared security depends on your vigilance. You can protect yourself by avoiding engagement with phishing attempts, and you can help protect all of us by swiftly reporting these threats to our office. When you report a phishing attempt, our office works quickly to block the threat from our system, minimizing its impact on our community. Your participation is key to our shared security, and we appreciate all that you do to help keep WashU secure.
Below, you will find an example of a common strategy for a phishing attempt.
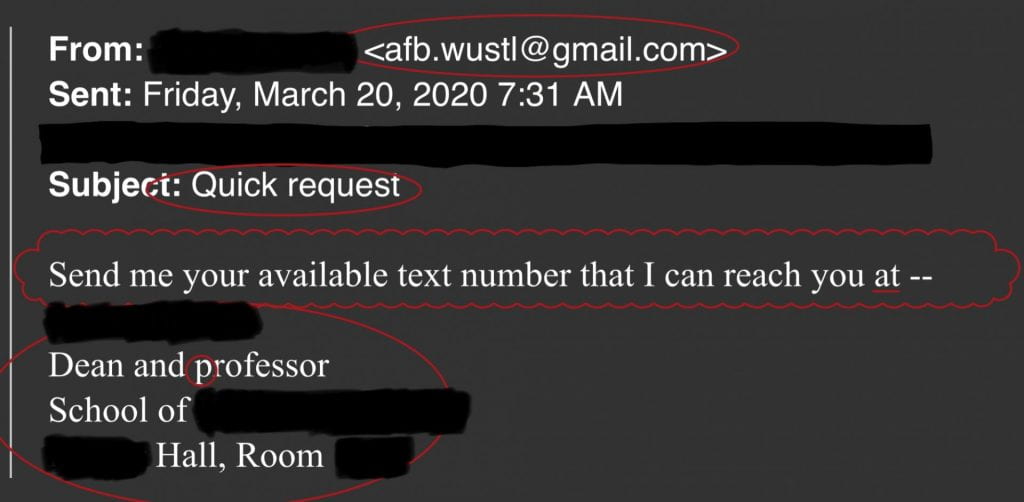
This is an “impersonation” phishing attempt. In impersonation attempts, cybercriminals impersonate known, often prominent, people to trigger the recipient’s quick action.
Fortunately, it is often easy to differentiate the impersonation from an authentic email. Let’s take a close look at the example above:
- The email address is not an authentic ‘@wustl.edu’ address but is instead a Gmail address that includes ‘wustl’ before the ‘@ ‘symbol. This is a typical strategy that criminals use to fool unsuspecting recipients who are quickly working through their email inboxes. Taking the time to check the sender’s address on any suspicious email is a simple and effective way to avoid becoming the victim of a phishing attempt.
- The subject of this email implies urgency, a common tactic in phishing campaigns. Criminals want their victims to make quick and careless decisions. If you receive emails that purport to be urgent, please exercise additional caution and check the email carefully for authenticity.
- Grammar and punctuation problems are additional clues that this is not an authentic email from a WashU dean. The only ‘sentence’ in the email ends in a preposition and does not include punctuation.
- The email signature is also a red flag—it does not follow the WashU branding guidelines, it contains only easily available public information, and it contains errors.
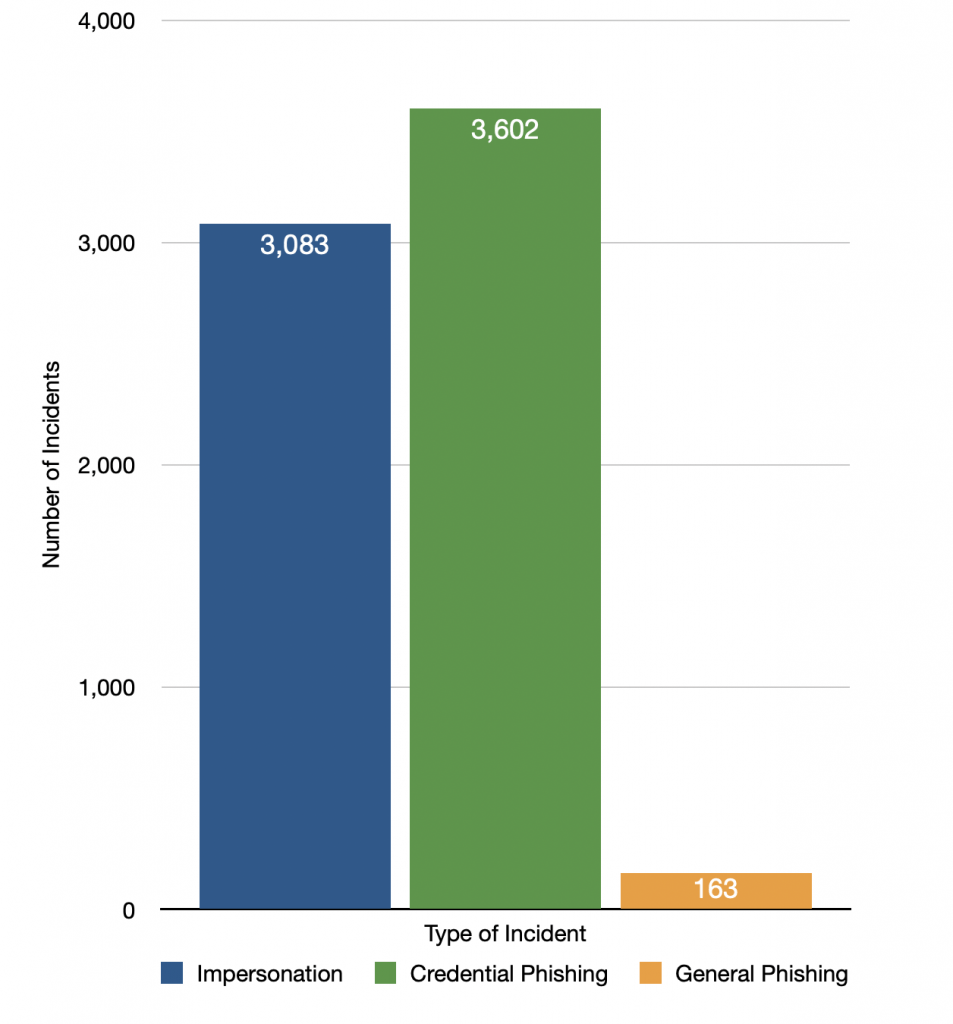
As illustrated in the bar chart below, impersonation is one of the most common types of attacks we encounter at WashU, with deans, department chairs, and university leaders typically impersonated. In the past year, we have intercepted more than 3,000 impersonation attempts. Credential phishing, which includes attempts to trick users into supplying login credentials, is also typical at WashU.
Number of Phishing Incidents by Type
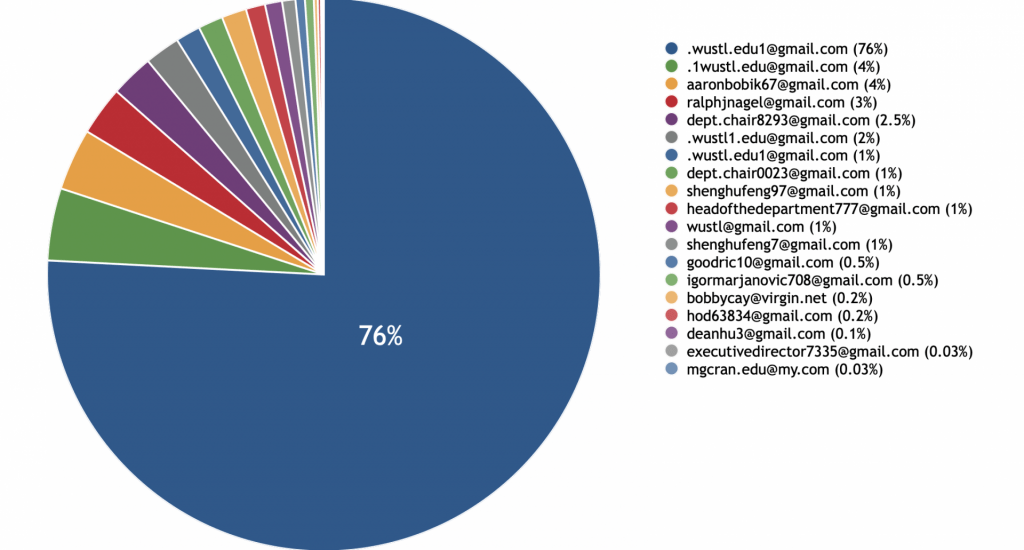
The most commonly impersonated email address during the past year is ‘.wustl.edu1 @gmail.com’, accounting for more than 76% of impersonations. Please be on guard against this sender. Other common impersonations originate from senders pretending to be university personnel, as illustrated in the pie chart below.
Impersonations by Email
If you ever receive a suspicious email, please protect yourself. Don’t reply, don’t download anything, and don’t click any links. Simply forward the message to the Office of Information Security (phishing@wustl.edu) and delete it from your inbox. If you receive a suspicious email from a known sender, verify the email’s authenticity by contacting the sender directly using known contact information (i.e., NOT the contact information contained in the email).
Thank you for your ongoing effort to protect yourself and our institution from cyber attacks. We appreciate all that you do to help keep WashU secure.