Letter from the CISO, Vol 2 Issue 2 Washington University Community: Why Do Cars Have Brakes? Why do cars have brakes? The obvious answer is that it helps them slow down and stop. The “real” counter-intuitive reason is that brakes let cars go fast. Imagine the panic and fear of being in a car that […]
Tag: Newsletter Volume 2 Issue 2
Identity Theft: Unflattering Imitation

Identity theft is nothing new. The term itself dates back to 1964 – a time exclusive to physical theft of documents like social security cards, credit cards, and driver’s licenses. These days, much of our personal information is on the internet. Due to the pandemic’s restrictions, more people used the internet for activities they would […]
Wonderful OneTrust

The Information Security Governance, Risk, and Compliance (GRC) team, led by Assistant Director, Denise Woodward, handles many types of security-related requests from the WashU community. When researchers need a security review of the tools they’re using for a study, when a department wants to adopt new technology, or when someone requires a specialized solution for […]
QR Codes: How Safe are They?

Quick Response Codes (QR codes) are increasingly popular, especially since most people no longer need a third-party app to scan them. During the Super Bowl last year, cryptocurrency company Coinbase spent millions of dollars on an ad that simply featured a QR code displayed on the screen. That ad became one of the most talked […]
Vulnerability Management Project: Expanded Server Protection

Overview The WashU Information Security team is actively engaged in keeping our network and data safe. Through the Security Vulnerabilities Project, one of the team’s main objectives is to expand server protection throughout WashU. Why A recent serious security incident was detected early because a server had the WashU Falcon CrowdStrike sensor installed. Due to […]
Chance to Win $100 in Our Monthly Challenge

The OIS is always looking for ways to improve your security and reward your participation in our efforts. This month, we want to point you towards a couple of resources that will help you protect yourself from cybercrime and understand how our office can support you. Guidance for Reporting Phishing Have you seen the Phish […]
Business Impact Analysis and Risk Assessment Reviews

Over the next several months, the Office of Information Security will conduct a Business Impact Analysis (BIA) and Risk Assessments (RA) on 24 important and critical applications. The BIA is essential to building an effective framework for a Business Continuity Plan. The goal of the BIA is to identify critical functions of the organization and […]
Scam of the Month: Fake (Real) Invoice Scam
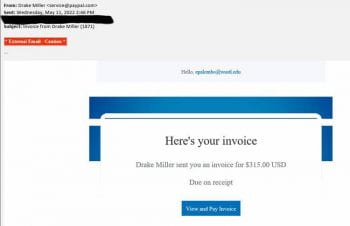
The Office of Information Security has observed a trend where criminals are sending fraudulent invoices to unsuspecting victims in hopes that they will be paid without the recipient noting that they are part of a scam. The tricky part of this particular scam is that the invoices are actually generated by payment handlers like PayPal. […]
Meet Your InfoSec Team: Brett McFadden, Information Security Analyst II

Brett McFadden, Information Security Analyst II, originally wanted to be a website designer. After taking a few classes in web development, he concluded that CSS – a style sheet language used by effective web developers – can only be understood by “wizards.” After consulting with a friend, Brett decided to investigate the cybersecurity program at […]