Letter from the CISO, Vol 1 Issue 11 Washington University Community: There are only two things to worry about—that things will never get back to normal, or . . . that they already have. In other words, the only constant in life is change, and Information Security is no exception. I sometimes worry that I […]
Tag: Newsletter Volume 1 Issue 11
Cybersecurity and the Supply Chain

You’ve undoubtedly heard the term “supply chain disruption” more times than you can count lately. The past few years have been fraught with disruptions—labor shortages caused by COVID-19, warfare, tropical storms and wildfires, factory fires, railroad transportation disruptions, and the six-day blockage of the Suez Canal. We’ve endured incredible upheavals, and many of these ultimately […]
Advice from a Graduating Student: Things to do as You Leave WashU

By Harrison Stites As members of our community graduate or otherwise move on from their time at WashU, it can be tempting to ignore or put off the things you need to do here as you look forward to the path ahead. WashU’s Office of Information Security offers you some tips and tricks to help […]
Avoid Phishing and Another Chance to Win $100 in Bear Bucks

The OIS is always looking for ways to improve your security and reward your participation in our efforts. This month, we want to point you towards a couple of resources that will help us identify and report potential phishing attacks. Have you seen the Phish Alert Button? It’s the easiest way for you to report […]
Scam of the Month: Important Payroll Message
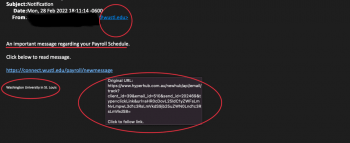
This month, we’re focusing on a particularly tricky scam. This one isn’t tricky because it’s complex on its surface; it actually relies on simplicity and brevity to lure in its victims. This scam mimics an important notification to trick recipients into handing over sensitive login information. It contains many hallmarks of a typical phish, but […]
Meet Your InfoSec Team: Jason Murray, Assistant Director and Architect of Digital Forensics and Incident Response

Jason Murray, Assistant Director and Architect of Digital Forensics and Incident Response, describes his role as the leader of “a team of talented Security Analysts who defend the university from cyber villains.” Throughout his career, he’s subscribed to the design principle, “build it secure,” considering the methods hackers might use to exploit flaws and access […]