Security researchers are warning of an uptick in phishing attacks targeting universities themed around COVID, Omicron, and testing information. These attackers seek to steal valuable information and often have the goal of tricking users into handing over their university (or other) log-in credentials.
Below, you will find an example of a phishing message using Omicron as part of its hook to lure in unsuspecting victims. Be sure to stay vigilant and keep an eye out for the warning signs of phishing in messages like the one below.
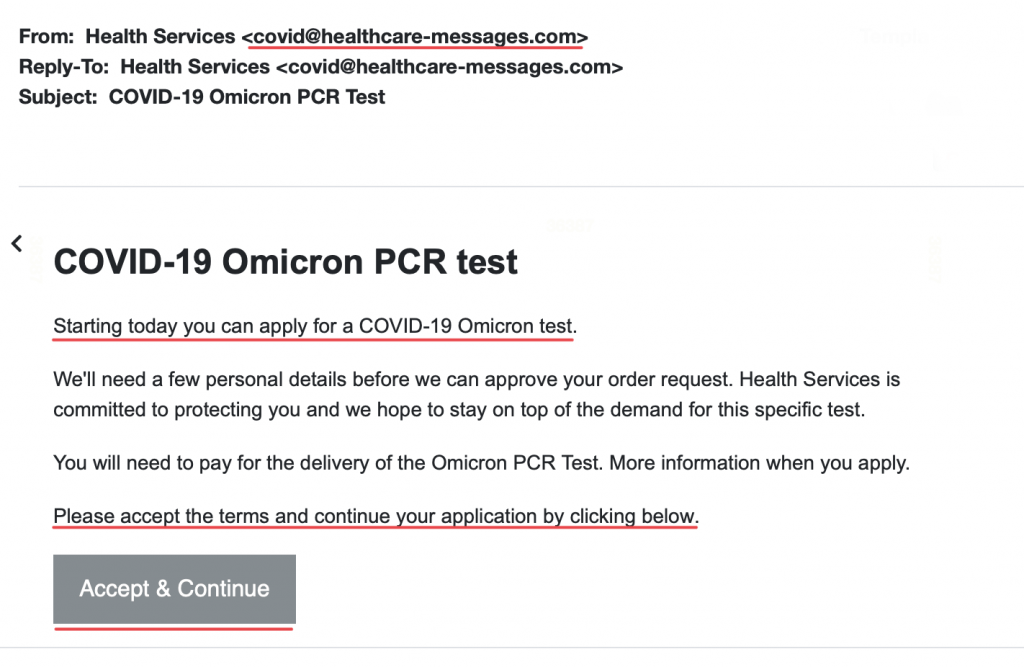
- This message contains a strange and suspicious email domain.
- The message seeks to entice the reader with a surprising offer of an Omicron test.
- The message tells the recipient to follow a link contained in the message.
- Hovering over this link reveals an unknown URL, directing users somewhere other than where the email says it will go.
The following phishing guidance applies to the threats described above along with and other common types of email phishing. As a general rule, be cautious if you receive any suspicious messages. Protect yourself by remaining calm and evaluating the message using the following safety tips.
10 Phishing Safety Tips
- Don’t click. Instead of clicking on any link in a suspicious email, type in the URL, or do a search on wustl.edu for the relevant department or page. Even if a website and/or URL in an email looks real, criminals can mask its true destination.
- Be skeptical of urgent requests. Phishing messages often make urgent requests or demands. When you detect a tone of urgency, slow down and verify the authenticity of the sender and the request by using official channels, rather than the information provided by the sender.
- Watch out for grammar, punctuation, and spelling mistakes. Phishing messages are often poorly written. Common hallmarks of phishing are incorrect spelling, improper punctuation, and poor grammar. If you receive an email with these problems, it may be a phishing attempt. Double-check the email address of the sender, don’t follow any links, and verify the authenticity of the request using official channels.
- Keep your information private. Never give out your passwords, credit card information, Social Security number, or other private information through email.
- Pick up the phone. If you have any reason to think that a department or organization really needs to hear from you, call them to verify any request for personal or sensitive information. Emails that say “urgent!”, use pressure tactics, or prey on fear are especially suspect. Do an online search for a contact phone number or use the contact number published in the WUSTL directory.
- Use secure websites and pay attention to security prompts. Always check if you are on a secure website before giving out private information. You can determine whether a website is secure by looking for the “https:” rather than just “http:” in the Web address bar or for the small lock icon in the Internet browser. If your browser cannot validate the authenticity of the website’s security certificate, you will be prompted. This is frequently a telltale sign of fraud, and it would be a good time to pick up the phone or report a suspicious message.
- Keep track of your data. Regularly log onto your online accounts and make sure that all your transactions are legitimate.
- Reset any account passwords that may have been compromised.
- Know what’s happening. Visit the Office of Information Security page ( https://informationsecurity.wustl.edu/home/alerts/ ) often and follow us on Twitter ( https://twitter.com/WUSTL_InfoSec ) to get the latest WashU Information Security Alerts.
- Report it. If you are a victim of an email scam, report it to our office by emailing infosec@wustl.edu ). When you report a phishing attack, we will investigate it and if necessary, remove other instances of the attack from our systems. Reporting the attack will help protect others and our institution.
Additional Resources
- Phishing | Office of Information Security | Washington University in St. Louis
- Phishing 101 | Office of Information Security | Washington University in St. Louis
- Whaling, SMiShing, and Vishing…Oh My! | Office of Information Security | Washington University in St. Louis
- Protect Yourself from Social Engineering | Office of Information Security | Washington University in St. Louis