Washington University will soon adopt Workday, a cloud-based software system for managing finances, human resources, and planning. The new system provides a single, integrated system for managing multiple facets of daily operations at WashU.
Background
WashU takes the security of your data and our systems seriously. Therefore, the system that we use to manage sensitive information such as personal and payroll data must demonstrate strong security. Workday offers several important security features. The software automatically encrypts all user data before it is stored in the database using the Advanced Encryption Standard and a unique encryption key for each customer. In addition, Workday uses Transport Layer Security to protect user access over the internet, preventing eavesdropping, tampering, and forgery. Our Workday implementation features Multifactor Authentication via WUSTLKey and WashU DUO 2FA to create a barrier to entry for credential phishers who may try to log into your account. Workday applications are hosted in secure data centers under constant surveillance, and the software company contracts with third-party firms that conduct regular vulnerability assessments of their systems. More information about Workday security features is available on the company’s website: https://www.workday.com/en-us/why-workday/security-trust.html .
Workday does its part to ensure the security of their software and systems, but cybercriminals continuously attempt to capture login credentials for these types of systems. The Workday system contains troves of sensitive personal information and is important to the daily operations of our institution. As such, it is an appealing target for cybercriminals who attempt to phish our users for login credentials with the goal of holding this vital data ransom or rerouting direct deposit payments. For example, in 2018 cyberattackers infiltrated the computer systems of Roadrunner Transportation Systems, Inc., a Wisconsin-based freight services company. According to Roadrunner’s lawyer, the hacker gained access to Workday by sending phishing emails to the company’s employees. In the attack, the hackers modified the direct deposit information of some employees. Fortunately, Roadrunner detected the changes before any funds had been transferred.
An Attractive Target
Cyberattackers are eager to get into systems like Workday, so it is crucial that each of us remains on guard for phishing attempts. Your vigilance is especially important during this rollout because our deployment dates are widely available online, providing potentially useful information to phishers who may attempt to attack our users and institution. We expect to be targeted by phishing attacks as we implement this new system, and we’re counting on you to help keep WashU secure by detecting and reporting phishing attempts.
Below, please find an example of a Workday phishing attempt. We’ve marked up the email, making note of every phishing red flag we detected.
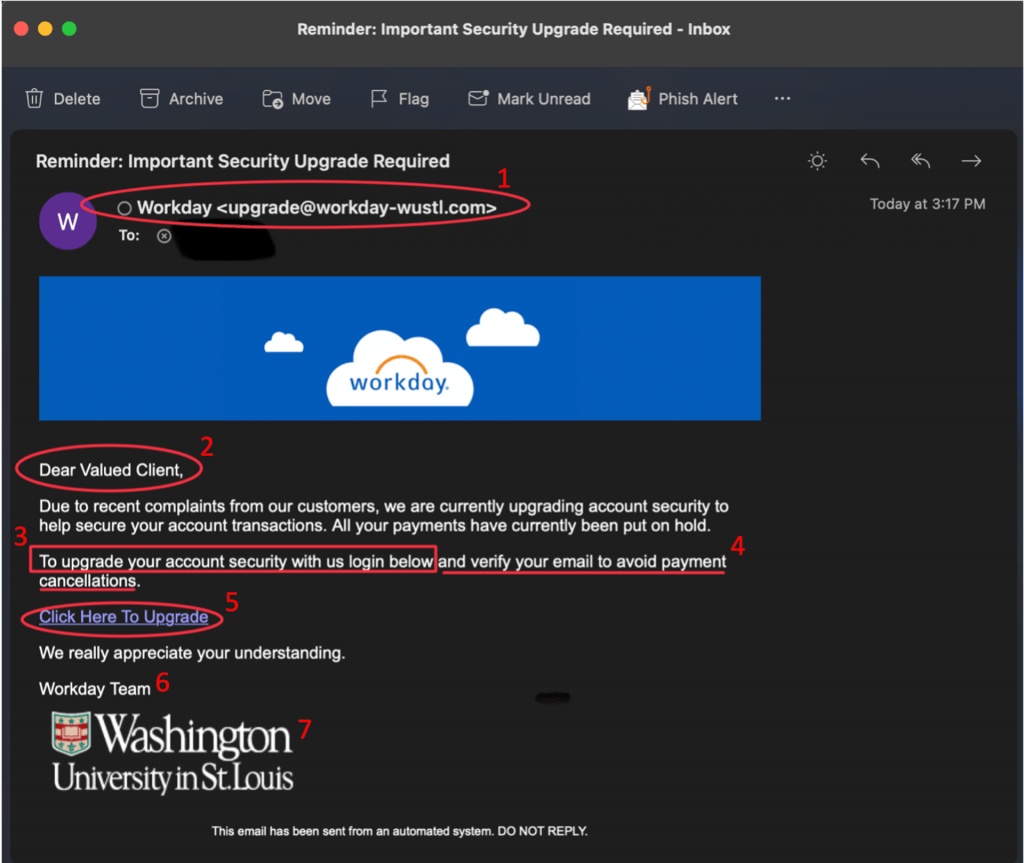
Red Flags from Example Above
- The sender’s email address is not consistent with the real Workday domain. Criminals often cleverly use domains that approximate real domains. In this example, the sender is using workday-wustl.com. The legitimate domain will be noreply-workday@wustl.edu. Be sure to look closely at the sender’s address for these subtle changes.
- The salutation is general and ambiguous.
- The email includes a request to follow a link. Instead of following a link in an email, go directly to the Workday site or log into your app. Legitimate messages will be available to you through these official channels.
- The email has a tone of urgency and threatens negative consequences. Legitimate requests from WashU will not use such a tone.
- Hovering over a link should reveal that the legitimate link points to https://workday.wustl.edu/. Look closely at the text between “https://” and the first single slash. For legitimate WashU sites, you will see a “.wustl.edu” immediately before the first single slash. There may be items following this first single slash, but the main area of concern is between “https://” and the first single slash. The address, https://workday.wustl.edu will redirect to mywokday.com. We also recommend that you bookmark and use One WUSTL at https://one.wustl.edu/ to ensure that you always find the authentic WashU Workday site for your daily access, rather than relying on links in emails.
- The signature does not include a WashU phone number. Legitimate communications from WashU entities should contain a WashU contact number in the signature for verification.
- Criminals can easily find and steal branding elements to make their phishing attempts seem authentic. The presence of an official logo does not guarantee the authenticity of an email.
For more information about safely checking and navigating links, please refer to the link guidance page on the Office of Information Security’s website.
When you see an email like this or are unsure of the authenticity of an email, please do not reply to it, click on any links, or engage with the attacker. Simply forward the message to the Office of Information Security at infosec@wustl.edu . Our information security team will investigate the message and remove all similar messages from our system, if necessary. Your vigilance is critical to the ongoing security of our systems.
Thank you for all that you do to help keep WashU Secure.