Phishing continues to dominate the cybercrime landscape and remains a major problem for organizations and individuals alike. The goal of many phishing attacks is to persuade the victim to click on a link, which could download malicious software or lead to a website built to harvest credentials and other personal information.
Hover over links
To see where a link is really directing you, hover your mouse over the link. Is it what it’s supposed to be?
For example, in an email claiming to be from your bank, does the provided link show your bank’s website when you hover over it?

Watch out for spoofed domains
Watch out for near misspellings in a URL, like ‘www.anazon.com’ or ‘www.wus.tl.edu’. These differences can be difficult to spot, so be sure to examine links closely for such errors.
Extend shortened URLs before clicking
URL shorteners convert long URLs into shorter, more manageable links. They also hide the their true destination. URL expanders help you see the final destination before you click. This way, you can avoid malicious websites that might steal your information or infect your device with viruses.
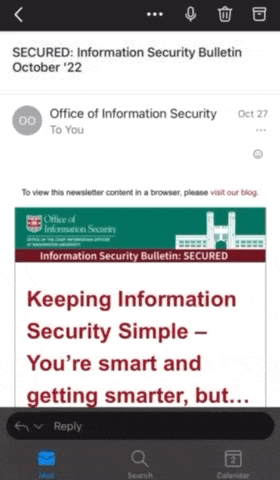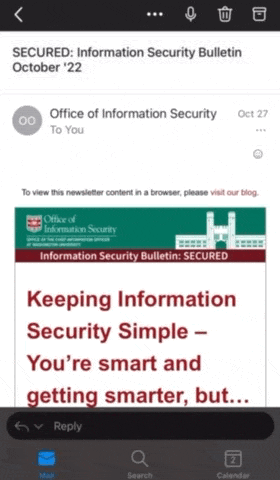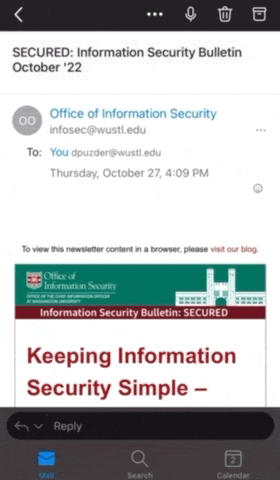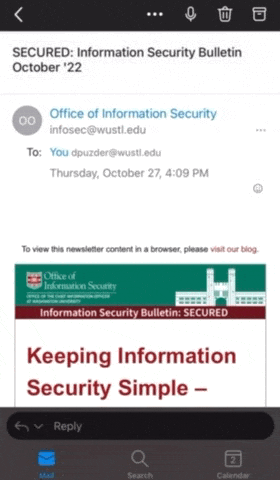
Verify the sender’s email address
In Outlook for mobile, the email address is not displayed by default. You can verify the sender’s email address by first opening the email and then tapping on the displayed name.
What To Do If You Receive a Suspicious Email
If you receive a suspicious email, please report it using the Phish Alert Button (PAB). When you report a phish using the PAB, our office will investigate the threat and take any necessary action, such as removing all similar messages from systems and notifying our community of the threat.