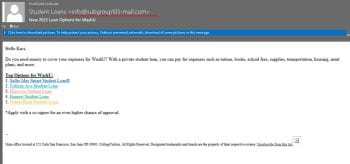
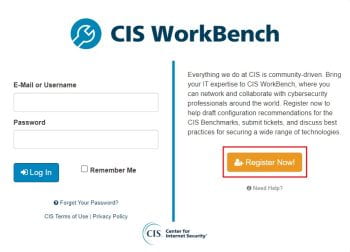
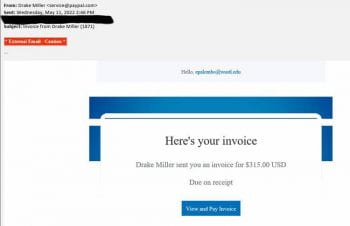
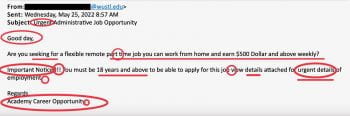
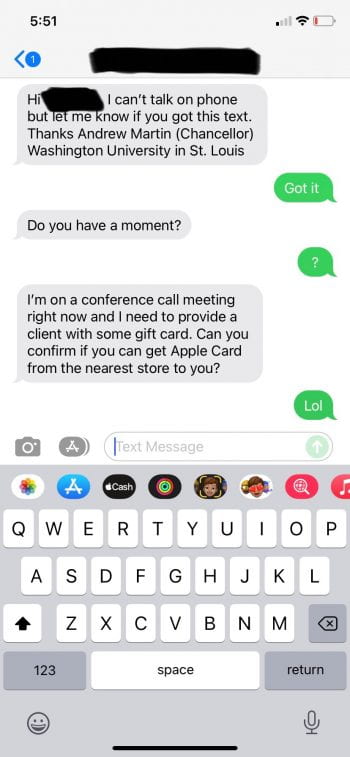
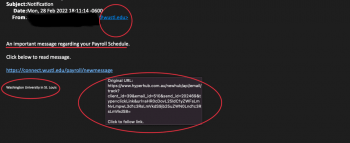
As school begins on campuses nationwide, criminals turn their attention to scams targeting students who are busy preparing for the upcoming semester. Criminals frequently rely on timely topics and strategies to exploit their victims. Below, you will find examples of real scam emails reported to our team within the last month. As we all gear […]
Scam of the Month: Student-Focused Scams