Before we get to our Scam of the Month for July, we wanted to take a minute to say thanks to one of our readers who took the time to reach out and provide some additional clues from last month’s column. Here is a link to our post from last month: https://informationsecurity.wustl.edu/scam-of-the-month-june-2021/
Our reader points out that the following clues could have been included in our list of phishing “red flags” for the scam email:
- The salutation included an email address that was not outward-facing (i.e., an email address that isn’t used for correspondence) and would never have been associated with the real contact info.
- The Norton branding wasn’t just missing. It was ‘wrong’ with the # symbols before and after the name.
Our reader went on to identify what they called “yellow flags,” or items that may appear in legitimate emails but that should arouse suspicion. These yellow flags are as follows:
- The use of an international version of the phone number
- The mismatch of the sender’s name and the name in the email address itself.
If you detect clues that you think we’ve missed in our Scam of the Month column, please reach out to us at infosec@wustl.edu, and we’ll do our best to compile them and share them in a future issue.
This month, we have an example of a Workday phishing attempt. We’ve marked up the email, making note of every phishing red flag that we detected.
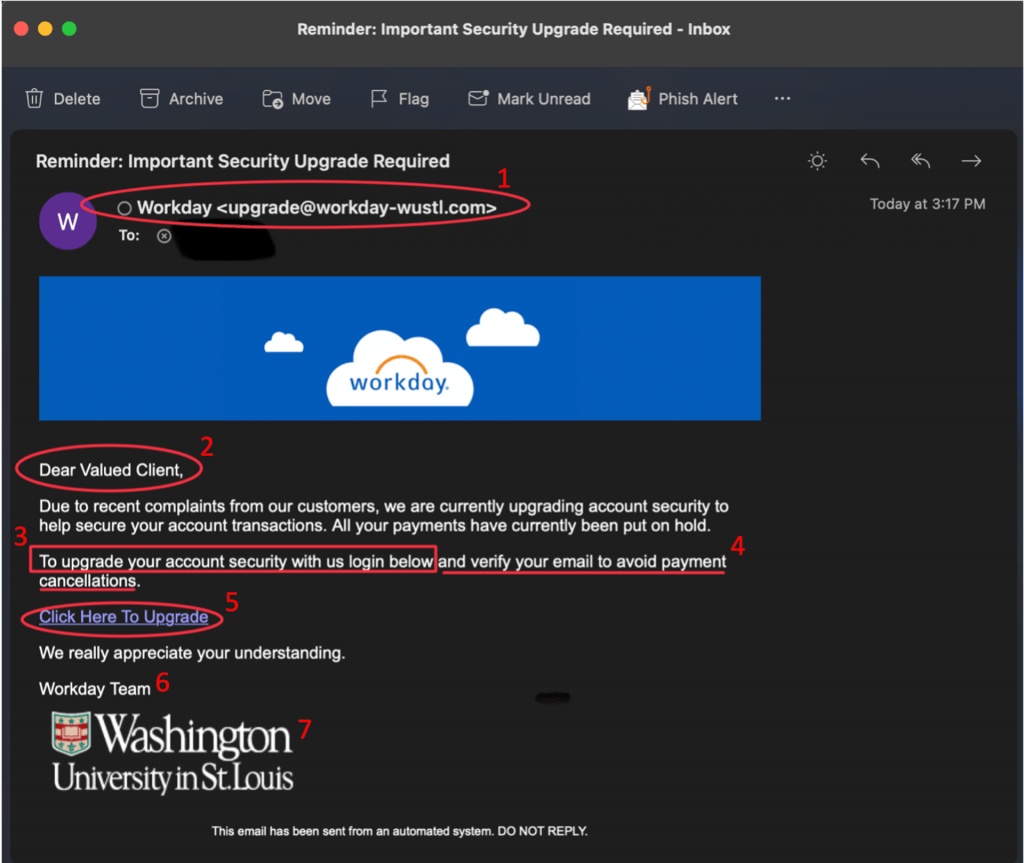
Red Flags from Example Above
- The sender’s email address is not consistent with the real Workday domain. Criminals often cleverly use domains that approximate real domains. In this example, the sender is using workday-wustl.com. The legitimate domain will be noreply-workday@wustl.edu. Be sure to look closely at the sender’s address for these subtle changes.
- The salutation is general and ambiguous.
- The email includes a request to follow a link. Instead of following a link in an email, go directly to the Workday site or log into your app. Legitimate messages will be available to you through these official channels.
- The email has a tone of urgency and threatens negative consequences. Legitimate requests from WashU will not use such a tone.
- Hovering over a link should reveal that the legitimate link points to https://workday.wustl.edu/. Look closely at the text between “https://” and the first single slash. For legitimate WashU sites, you will see a “.wustl.edu” immediately before the first single slash. There may be items following this first single slash, but the main area of concern is between “https://” and the first single slash. The address, https://workday.wustl.edu will redirect to mywokday.com. We also recommend that you bookmark and use One WUSTL at https://one.wustl.edu/ to ensure that you always find the authentic WashU Workday site for your daily access, rather than relying on links in emails.
- The signature does not include a WashU phone number. Legitimate communications from WashU entities should contain a WashU contact number in the signature for verification.
- Criminals can easily find and steal branding elements to make their phishing attempts seem authentic. The presence of an official logo does not guarantee the authenticity of an email.
For more information about safely checking and navigating links, please refer to the link guidance page on the Office of Information Security’s website.
When you see an email like this or are unsure of the authenticity of an email, please do not reply to it, click on any links, or engage with the attacker. Simply forward the message to the Office of Information Security at infosec@wustl.edu. Our information security team will investigate the message and remove all similar messages from our system, if necessary. Your vigilance is critical to the ongoing security of our systems.
Thank you for all that you do to help keep WashU Secure.